Sysdig Secure and Google Security Command Center Integration – Why, What, How

Sysdig and GCP Partnership
Sysdig Secure and the GCP Ecosystem
Sysdig is a premier Google Cloud Platform (GCP) partner and has been working with Google towards the common goal of supporting our customers and securing their cloud journey for the last seven years. Sysdig is focused on securing and monitoring workloads running on Google Cloud – including Google Kubernetes Engine (GKE), Autopilot, Anthos, and more. All these various elements of GCP can be protected using Google Security Command Center. Learn more about how to enhance your GCP security.
The Sysdig platform provides visibility and security built on Falco, Sysdig OSS, and Open Policy Agent (OPA), which are the open standards for runtime threat detection and policy management. You can spin up a Sysdig account on GCP to quickly get started.
Sysdig Secure with Google Security Command Center
To better serve our customers, Sysdig has now integrated with Google Security Command Center so that you can send Sysdig-enriched events to Google SCC as part of your incident troubleshooting and remediation workflow.
Google Security Command Center is GCP’s premier security and risk management platform, allowing you to:
- Gain centralized visibility and control
- Discover misconfigurations and vulnerabilities
- Report on and maintain compliance
- Detect threats targeting your Google Cloud assets
Sysdig Secure provides an event-forwarding feature that can send security data onward to different security and risk management platforms. For Google’s SCC, Sysdig Secure is able to provide enriched runtime cloud events, giving you added visibility and context.
Bryan Smoltz, (VP of Technology Alliances, Sysdig) states: “Our integration with Google’s SCC allows our customers to visualize Sysdig events directly on their SCC portal. Looking at these events, security teams are able to confidently investigate suspicious activity and correlate it with the happenings within the broader GCP ecosystem.”
Speed up your security operations with Sysdig Secure
Alert triage involves steps to gauge the event’s severity and launch an appropriate incident response. Sysdig has a feature known as “in-use” which shows what vulnerabilities currently exist in the images deployed to production and if these vulnerabilities have known exploits. This reduces the number of vulnerabilities to fix by almost 95% leading to quicker prioritization. Using Sysdig Secure as a part of your SOC speeds up:
- Vulnerability prioritization
- Alert triage processes
- Incident response activities
How do we set up the integration?
(The following steps showcase how to leverage Sysdig Secure with Google’s SCC. Although working, this integration is in beta and not officially supported by Sysdig yet as we are still carrying out rigorous testing with it.)
We validated a proof-of-concept for connecting Sysdig Secure with Google SCC. Follow the below-mentioned steps to quickly integrate these two security systems. Or check out the Sysdig Secure product documentation here.
1. Set up Sysdig Secure account
It’s easy to get started with Sysdig Secure. Just go to Start Free Trial | Sysdig to begin with a free 30-day trial.
2. Access Google’s SCC
You can do this by logging into the GCP console and navigating to the Security Command Center.
3. Prerequisites: IP whitelisting, Enabling APIs for SCC, Service Accounts
In the GCP console enable the SCC API and the IAM API. Update your firewall and allow inbound requests from these Sysdig Event Forwarder IP addresses to enable Sysdig to handle event forwarding. A service account with the right permissions is required that can be uploaded to the Sysdig UI.
4. Set up the Google SCC integration within Sysdig
Within Sysdig Secure, go to “Settings” > “Event Forwarding” and select “Add Integration.” Choose SCC. Then, enter the integration name, the workspace ID, and the secret key. Also, select runtime events as the data types you wish to forward to Google SCC.
5. Dive into the event details on Google SCC
Now, you can explore and investigate suspicious activity detected by Sysdig Secure within SCC.
Proof of concept: Generate events to be detected by Sysdig & forward to SCC
Once the integration is done, Sysdig Secure will be able to forward any cloud-related event to the Security Command Center.
1. Generate an event on your GCP
1) For our testing purposes, we generated a security event that involved deleting a GKE cluster via console UI/CLI. The event together with its context gets captured and shown in the Sysdig UI as follows: (In the image below: “Insights > Cloud Activity” dashboard)
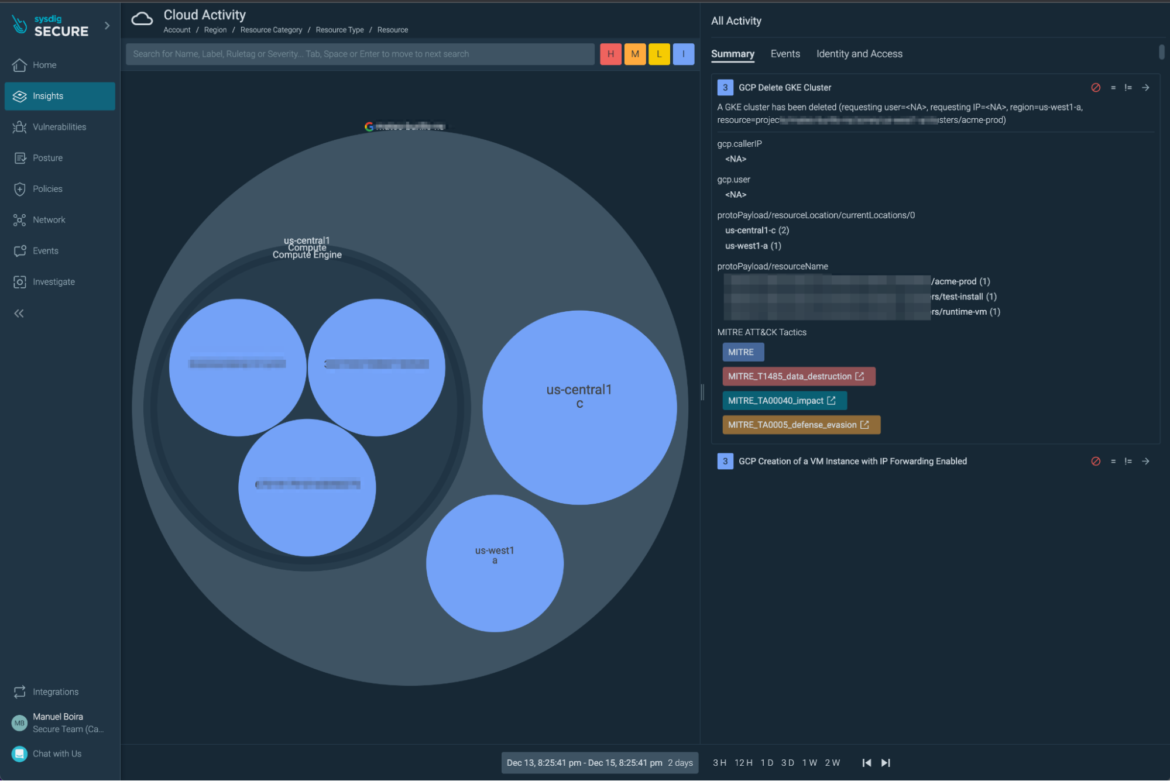
2. View the event on your SCC UI
We can now verify that the same events appear on our Security Command Center UI. To locate them easily, the option “SOURCE TYPE > Sysdig” can be checked.
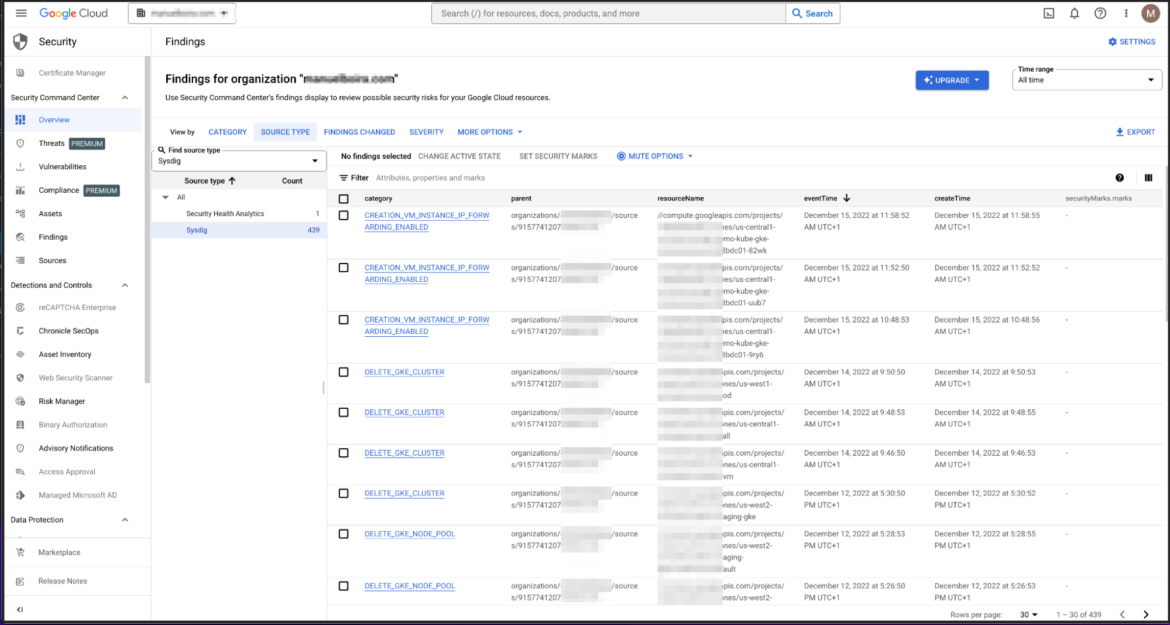
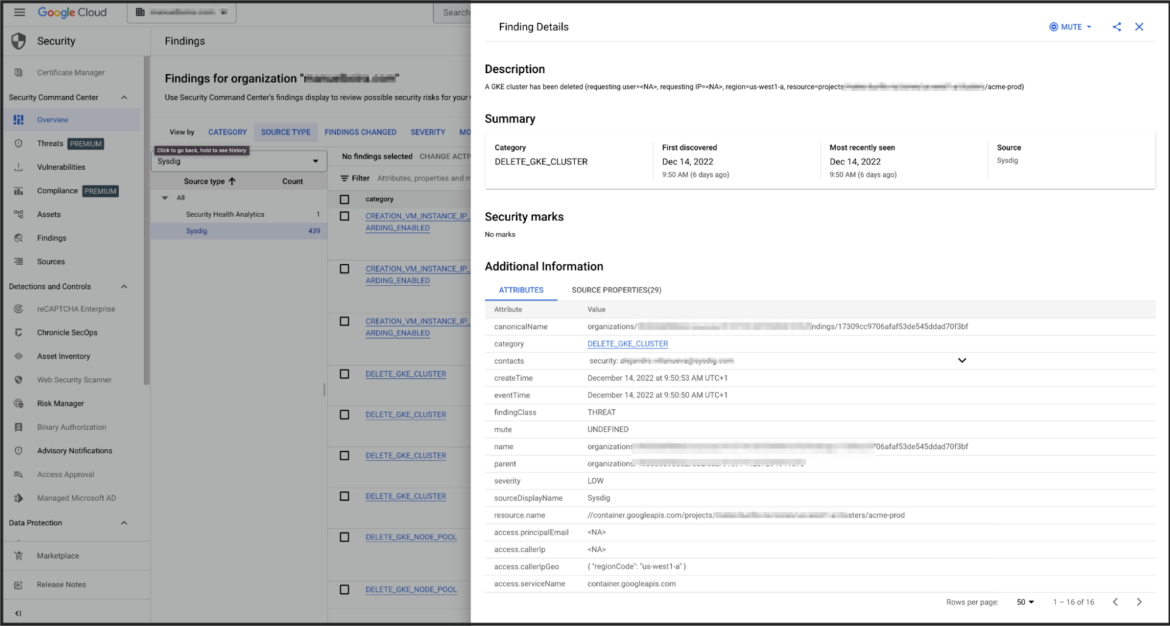
3. Expand details of the event on your SCC UI
We can click on any event to expand on its details within SCC. SCC allows us to check the context of the finding.
Other resources
Sysdig and GCP Partnership

